How to Set Up Single-Sign-On with Active Directory (ADFS)
Follow the instructions below to set up SAML 2.0 through ADFS for your organization.
Prerequisites for setup:
- Administrator access to your organization’s LearnPlatform account
- ADFS Administrator access through your organization to process SAML Single-Sign-On correctly
- Your organizations subdomain must be listed in LearnPlatform's setting configurations.
To set up Single Sign-On, please follow the steps below:
Configuring LearnPlatform Account (Part 1)
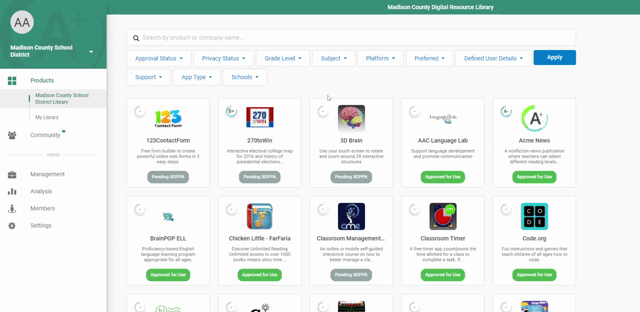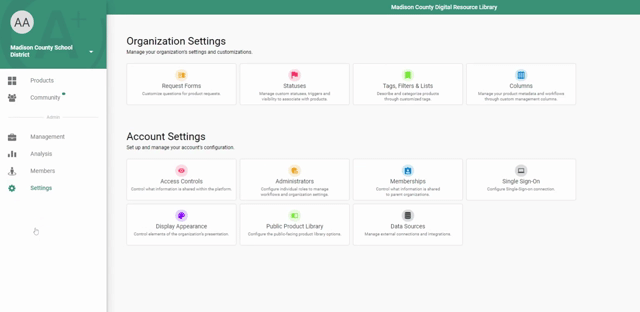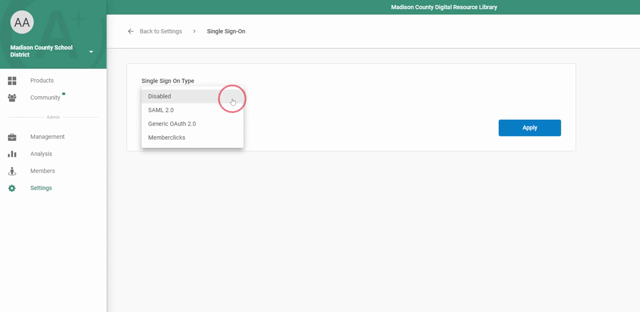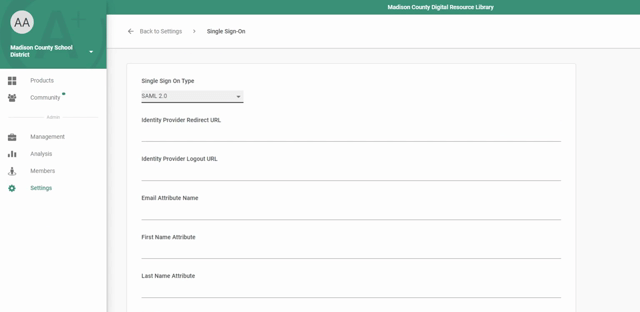
- Sign in to your LearnPlatform administrator account, and click on Settings > Single Sign On > Single Sign On Type > SAML 2.0
- Toggle “ON” the “Use organization domain for callback urls” at the bottom of your Single-Sign-On page.
Configuring ADFS
- On a separate window or tab, sign in to your ADFS Management dashboard.
- Go to Trust Relationships > Relying Party Trusts
- Select option “Import data about the relying party published online or on a local network”
- Click 'Add Relying Party Trusts' and add LearnPlatform’s metadata address:
- The address will be
https://subdomain.app.learnplatform.com/users/auth/saml/metadata/replacing “subdomain” with your LearnPlatform subdomain.
- The address will be
- Select “Next” and then specify any display name you would like or leave as default name
- Select “Next” and then select 'Permit all users to access this relying party'
- Select “Finish” - you should now see LearnPlatform (or your chosen display name) displayed as a Relying Party Trust
- Right-click on the displayed name and select “Add Rule”
- Choose “Send LDAP Attributes as Claims”
- Select “Next” and then specify any display name you would like for the Claim Rule Name or leave as default name
- Select Active Directory as the Attribute store
- For the LDAP attribute, select “SAM-Account-Name”
- For the Outgoing Claim Type, select “Name ID”
- A new row will appear that will allow you to map attributes you would like to send through the connection
- The left input will contain the attribute you’d like to send
- The right input will contain the field that LearnPlatform will match to that data
- Example completed attribute mapping
LDAP Attribute
Outgoing Claim Type
Surname
LastName
Given-Name
FirstName
E-Mail-Addresses
email
You will personalize the LDAP attribute and Outgoing Claim Type based on your specific Active Directory settings for your district. - Select “Finish” to complete the ADFS setup.
- While still in the ADFS Management console, find the Find your Metadata URL
- Browse to Service > Endpoints > Metadata > Type: Federation Metadata. It should take the format:
https://<ADFS server name>/federationmetadata/2007-06/FederationMetadata.xml - Copy the Metadata URL to your clipboard
Configuring LearnPlatform Account (Part 2)
- Browse to Service > Endpoints > Metadata > Type: Federation Metadata. It should take the format:
- Copy and Paste the Redirect URL* to the Identity Provider Redirect URL field in back in your LearnPlatform SAML 2.0 setup page. (Settings > Single Sign On > Single Sign On Type)
Finding the Redirect URL might mean opening the metadata link (i.e. https://<ADFS server name>/federationmetadata/2007-06/FederationMetadata.xml) and parse out the actual redirect URL. We are looking for the HTTP-Redirect Binding attribute.
- Go to LearnPlatform’s SAML setup page and enter the same attribute mapping fields as in your ADFS Management Console:
- In the ADFS Management Console, download or copy the app’s certificate and copy-paste the entirety of the certificate text to the Certificate field in the LearnPlatform SAML 2.0 setup page
Make sure not to include any spaces or change the formatting of the certificate. You must download the certificate into a text editor like NotePad or TextHelp. If you use another program, it may pull characters such as HTML into the certificate, which means it will not paste correctly.
LearnPlatform’s SAML 2.0 setup page
- Go to LearnPlatform’s SAML setup page and enter the same attribute mapping fields as in your ADFS Management Console:
- Go to LearnPlatform’s SAML setup page and copy the first callback url ending in “/callback/” at the bottom of your Single Sign-On page.
- In the ADFS Management console , select the LearnPlatform Relying Partner and go to the Endpoints tab and click on the Add SAML button at the bottom. Enter the following values:
- Endpoint type: SAML Assertion Consumer
- Binding: POST
- Index: 1
- Trusted URL: https://subdomain.app.learnplatform.com/users/auth/saml/callback/
- Click OK to save the new end point.
- Go back to LearnPlatform’s SAML setup page and copy the second callback url ending in “/metadata/”
- Go to your ADFS Management Console and paste the callback URL (ending in “/metadata/”) in the “Relying Party Trust Identifiers” field. Make sure you capture the backward slash (/) at the end and avoid any spaces. If the URLs are not complete, your setup may not work properly.
Set to ‘ON for everyone’ first, test the SSO, then go back and restrict access if necessary.
Please keep in mind that these settings may take up to 24 hours to propagate to all users.
Your link to login to LearnPlatform is now: https://[YOUR_SUBDOMAIN].app.learnplatform.com/users/sign_in/
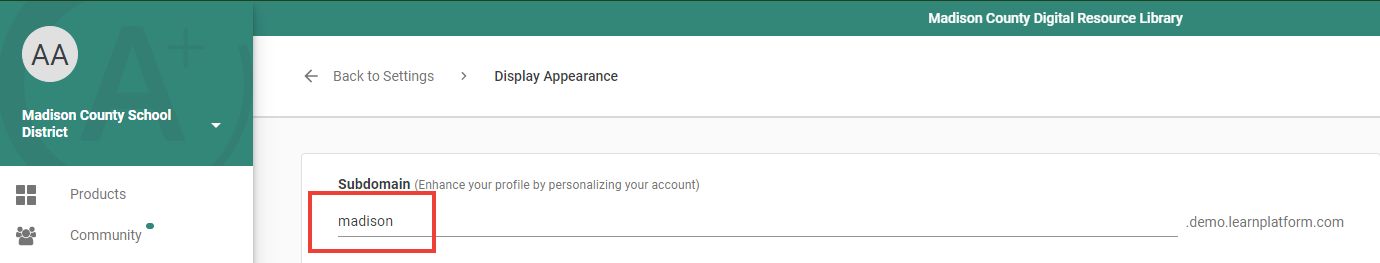
TIP: Your subdomain is located in LearnPlatform > Settings > Display Appearance
YOU ARE ALL SET!
